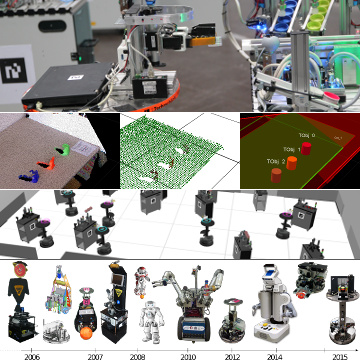
Our tutorial Cognitive Robotics in Industrial Settings Competitions has been accepted for AAAI 2018.
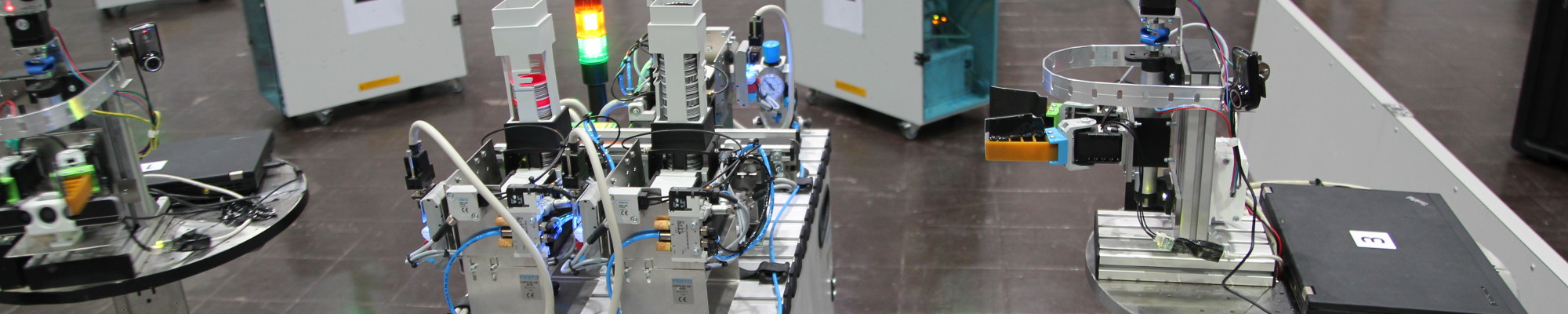 RoboCup Logistics League robot approaching Base Station
RoboCup Logistics League robot approaching Base Station
 Hybrid Reasoning: PR2 performing active perception
Hybrid Reasoning: PR2 performing active perception
 KBSG’s Caesar robot approaching dish washer
KBSG’s Caesar robot approaching dish washer
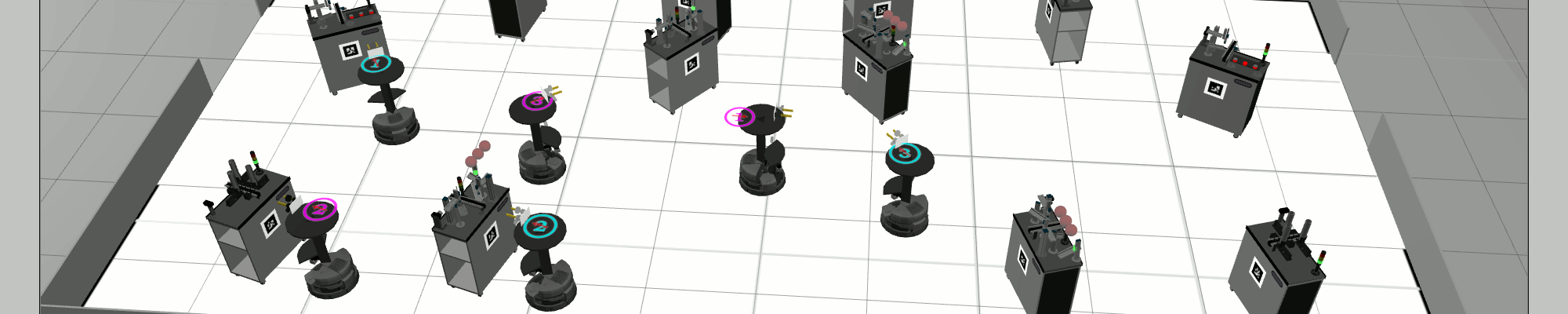 RoboCup Logistics League Simulation
RoboCup Logistics League Simulation